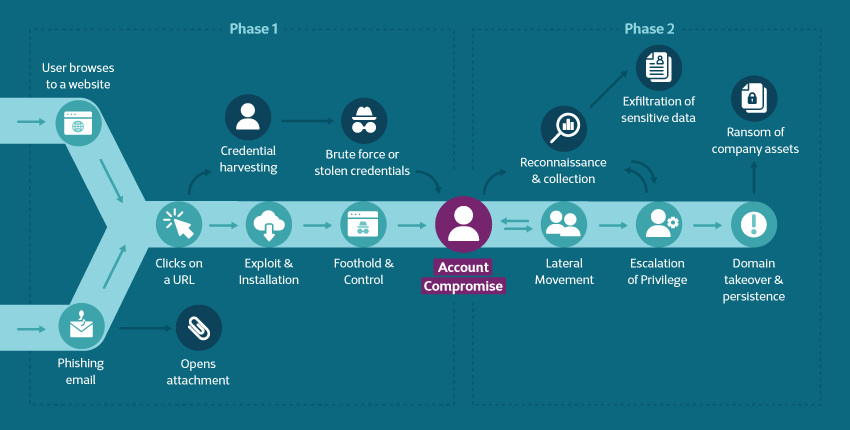
A cyberattacker needs various actions to successfully infiltrate a network and exfiltrate data from it. That sequence of actions is described in the cyber kill chain. Understanding this chain makes it easier to design and monitor a response plan to ‘kill’ it: prevent the attack or, in the worst case, minimize the damage done. Here’s what a cyber kill chain looks like:
Preventing a cyberattack: four categories
A cyberattacker may cause harm in different ways, via different channels. Make sure to prevent attacks by securing your:
- Devices: computers, mobile devices, servers, ...
- Applications: software, mobile apps, services, ...
- Identities: user accounts and credentials
- Data: documents, emails, ...
Infiltrating your network via email or browser
One of the first stages in the cyber kill chain is the intrusion step: the attackers are attempting to get a foothold in your network or device to then exploit existing vulnerabilities. 90% of all cyber attacks start with a phishing email. The phishing techniques used are diverse: from installing malware via a malicious email attachment and embedding an URL in an email that redirects you to an unsecure website to spoofing the sender address. More and more phishing attacks also include ransomware which freezes a company’s IT system in an attempt to generate ransom payments to the attackers.
90% of all cyberattacks start with an e-mail.
In addition, cybercriminals can also gain entry to your computer or other devices via your browser. Once they have forced their way in, they can manipulate or steal data or spread malicious code throughout the company network.
Open mails and attachments and click URLs without fear
Included in your Microsoft Office 365 E5 Security Plan, Microsoft Defender for Office 365 - the new name for Office 365 Advanced Threat Protection – helps disrupt sophisticated, malicious threats posed during this initial ‘infiltration phase”. The suite integrates a series of advanced capabilities that make use of machine learning to scan emails and block or flag emails, links or attachments that may corrupt your hard drive, steal your data or expose you to other types of fraud:
- Anti-phishing capabilities
When an email enters your inbox it is scanned by MS Defender for malware. Machine learning models evaluate the email to decide whether it is a malicious email. If so, the email is removed and the user and admin are notified. - Safe attachments
Emails with attachments are checked for malicious content: the file is routed to a special environment where it is automatically opened and tested, using machine learning models. If the file is found to be safe, it'll open as expected. If not, it will be removed automatically. - Safe links
If you receive an email containing an URL, the Safe Links feature will automatically check the URL before you click it. If the URL is safe, it'll open as usual. If not, a page will pop up warning you of a potentially harmful link.
Thanks to the dashboard functionality, your IT or security team gets insights on all the security incidents that occur – ready to take the appropriate action if needed.
First and foremost: raise employee awareness
In spite of all the Microsoft 365 technology you may use to defend your systems from malicious attacks, there is one important extra factor to take into account at all times: employee awareness. All it takes is one person, one time, to become careless to cause a data breach. So, first and foremost, educate your employees and conduct training sessions to make sure that they understand the types of attacks they may face. Inform them to be wary of e-mails with attachments from people they don't know. Let them know that no credible supplier, bank or website would ask for their password over e-mail and stress they need to be careful which browsers or cloud applications – e.g. Dropbox – they use.
All it takes is one person, one time, to become careless to cause a data breach. So, first and foremost, educate your employees and conduct training sessions.
Preventing identity breaches
When staff awareness is combined with effective technology, you have taken your first steps to prevent malicious e-mail attacks. Yet, what about preventing identity breaches and keeping hackers out of your system to prevent data theft or tampering? We’ll explain all about that second and third steps in our next blog posts on security in the digital workplace.

